Team Management
Service Owner vs Consumer
In NetOrca, teams are referred to as Consumers and Service Owners throughout the documentation.
However, this distinction does not imply that there are two separate types of teams.
Any team can act as both a Consumer and a Service Owner, depending on the ownership of resources.
- If a team owns a Service, they are considered Service Owners.
- If a team submits a declaration that includes Applications and Service Items, they become Consumers, as they own those resources.
Create a new Team
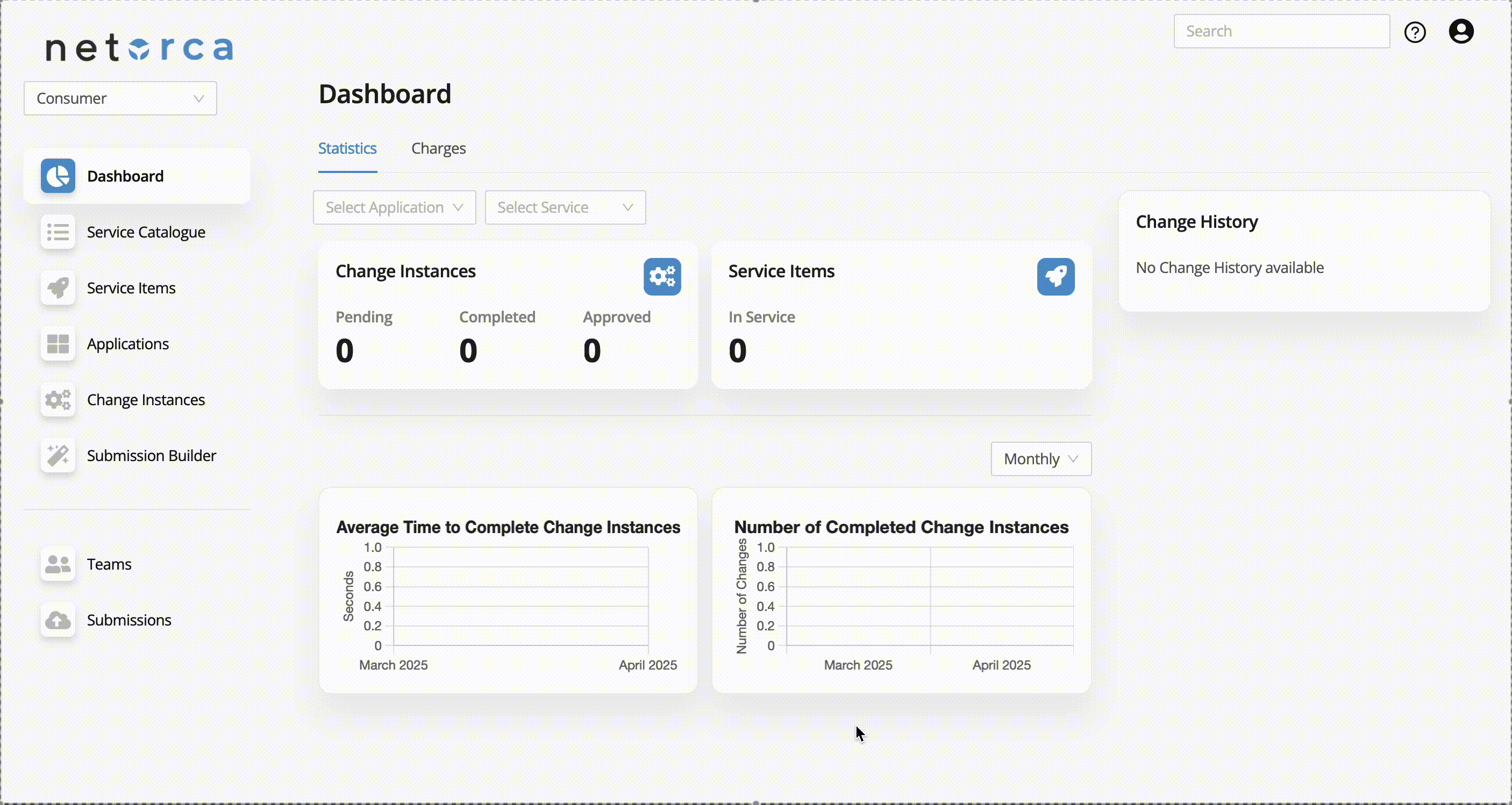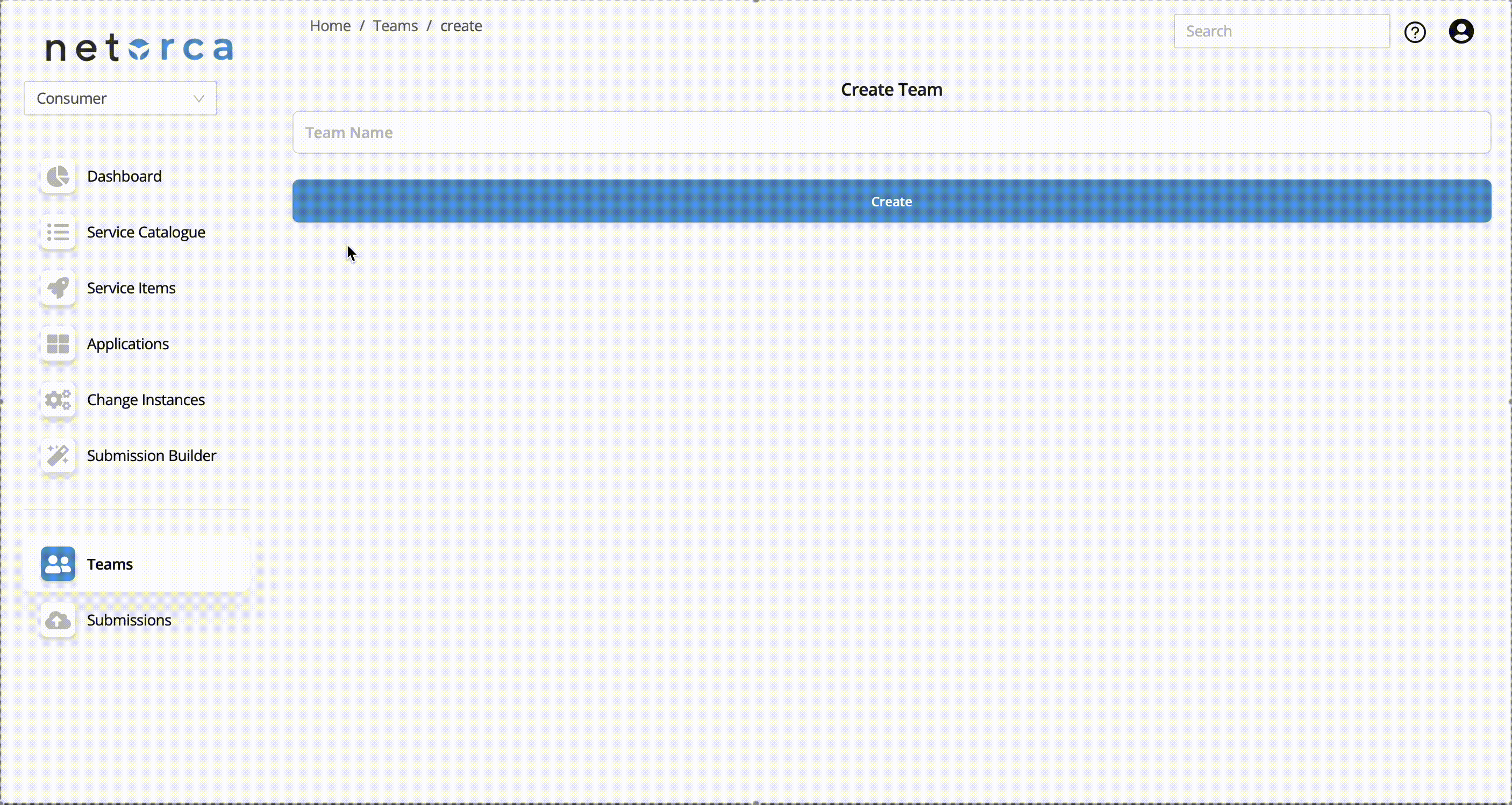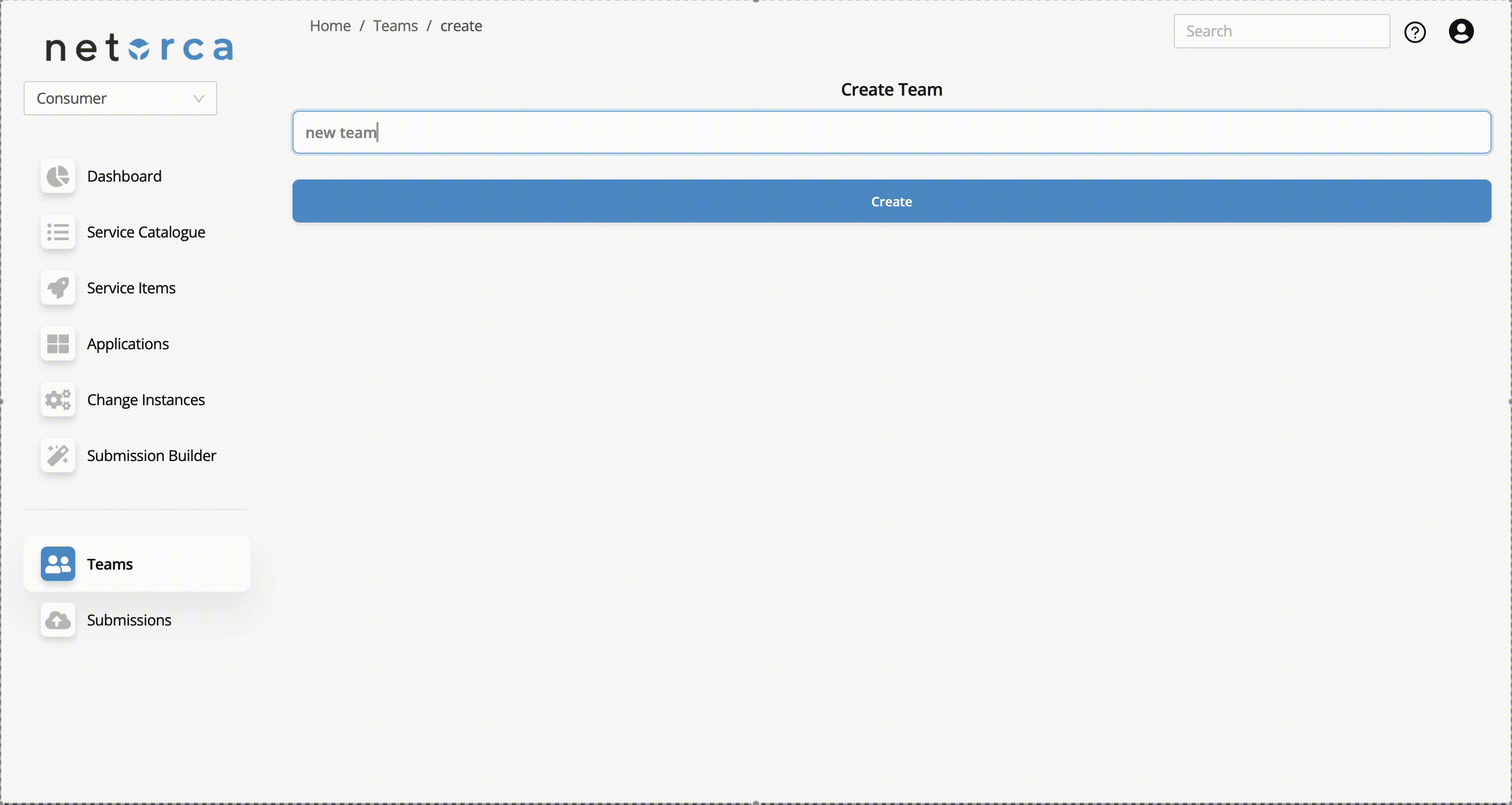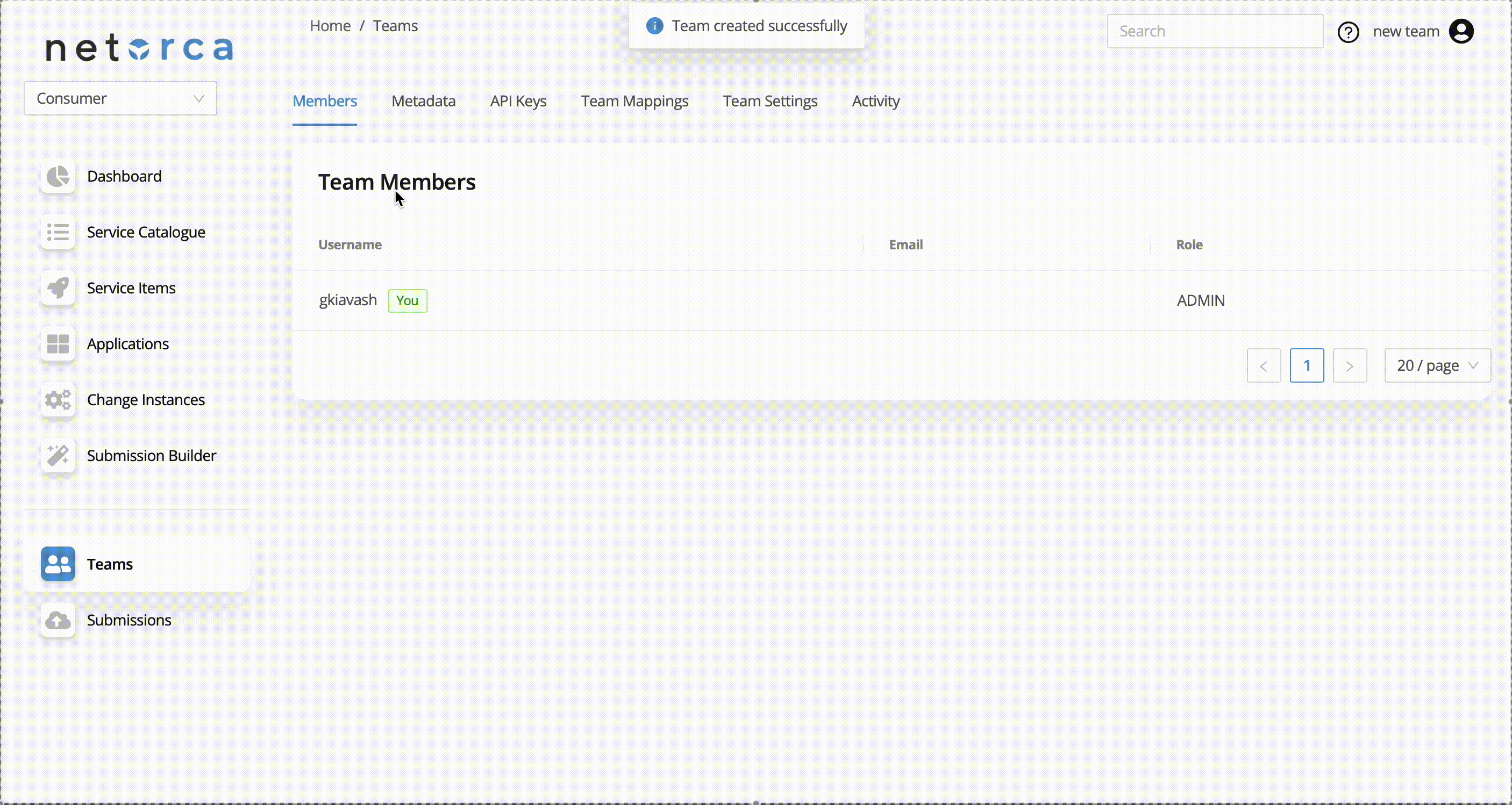
Each user can create a new team in NetOrca. Upon creation, the user automatically becomes the team's Admin. To create a team:
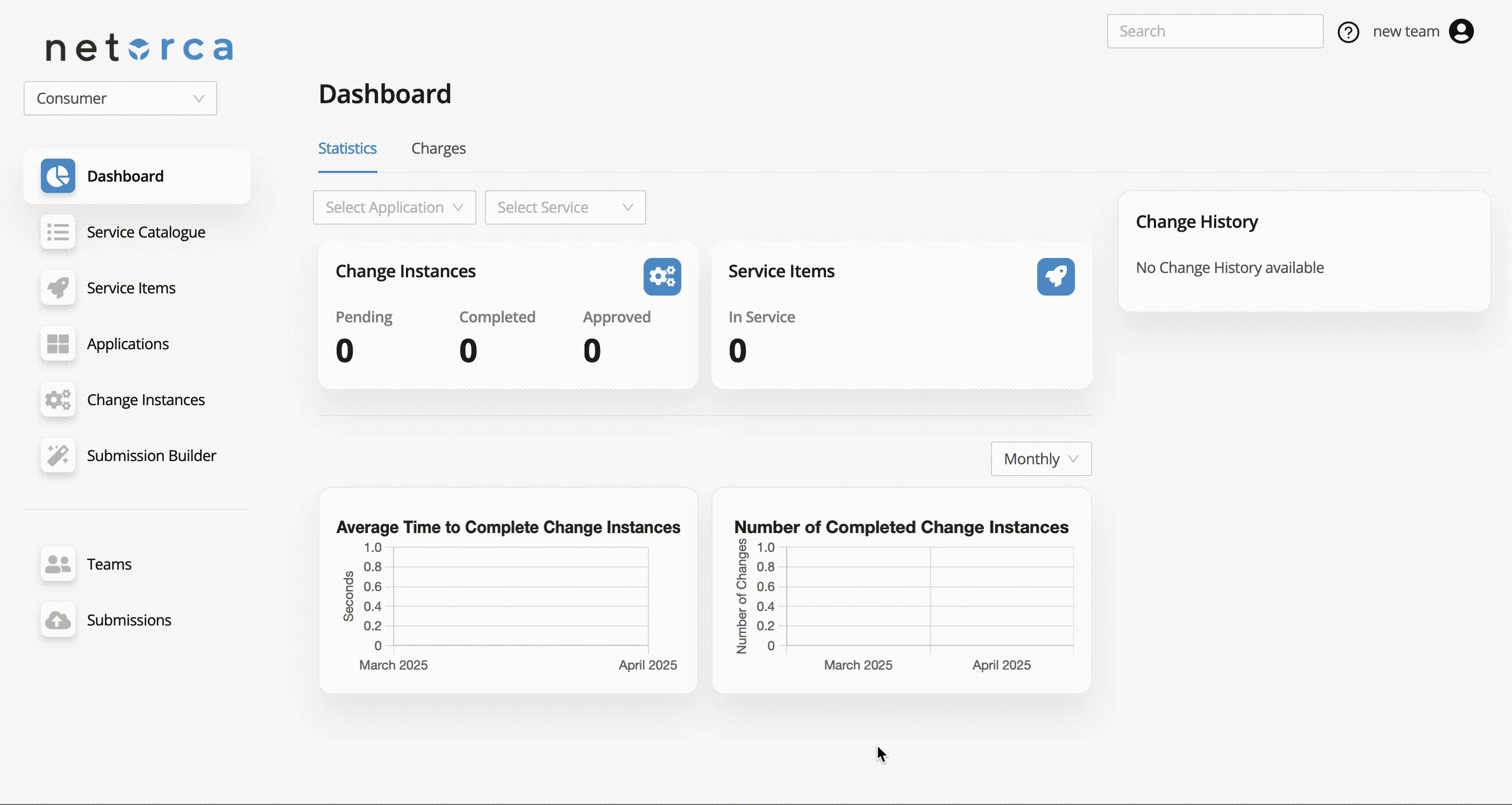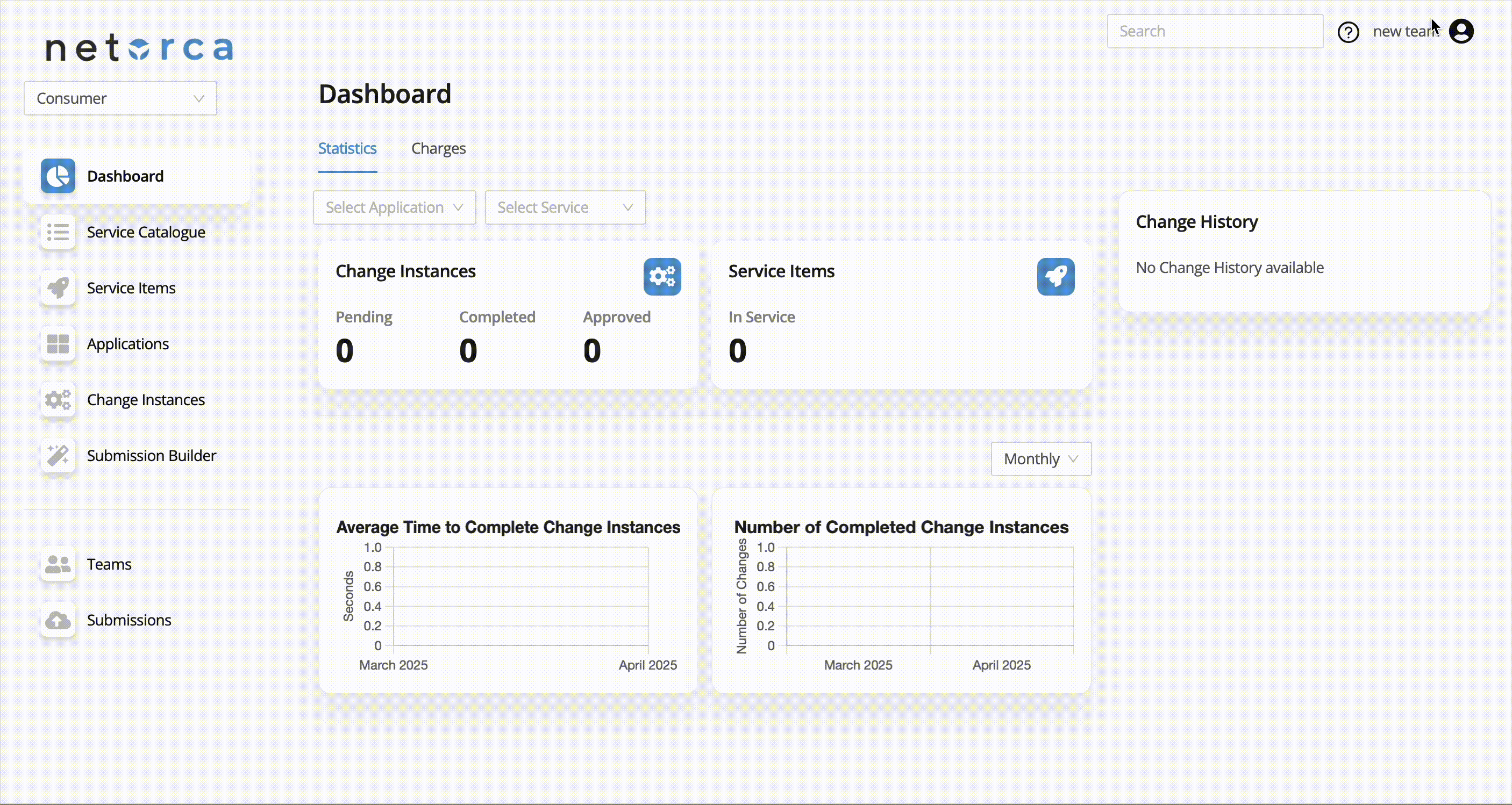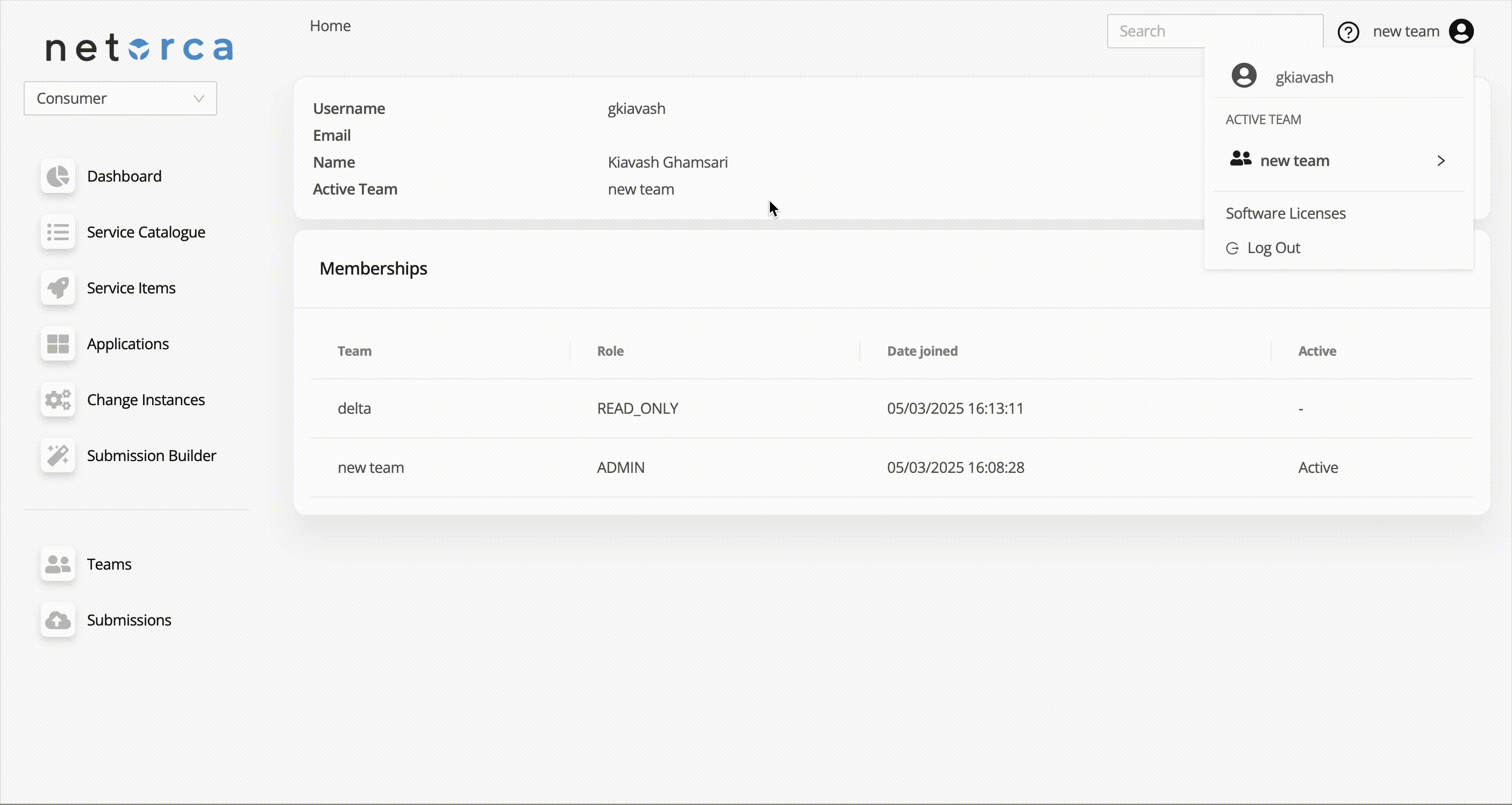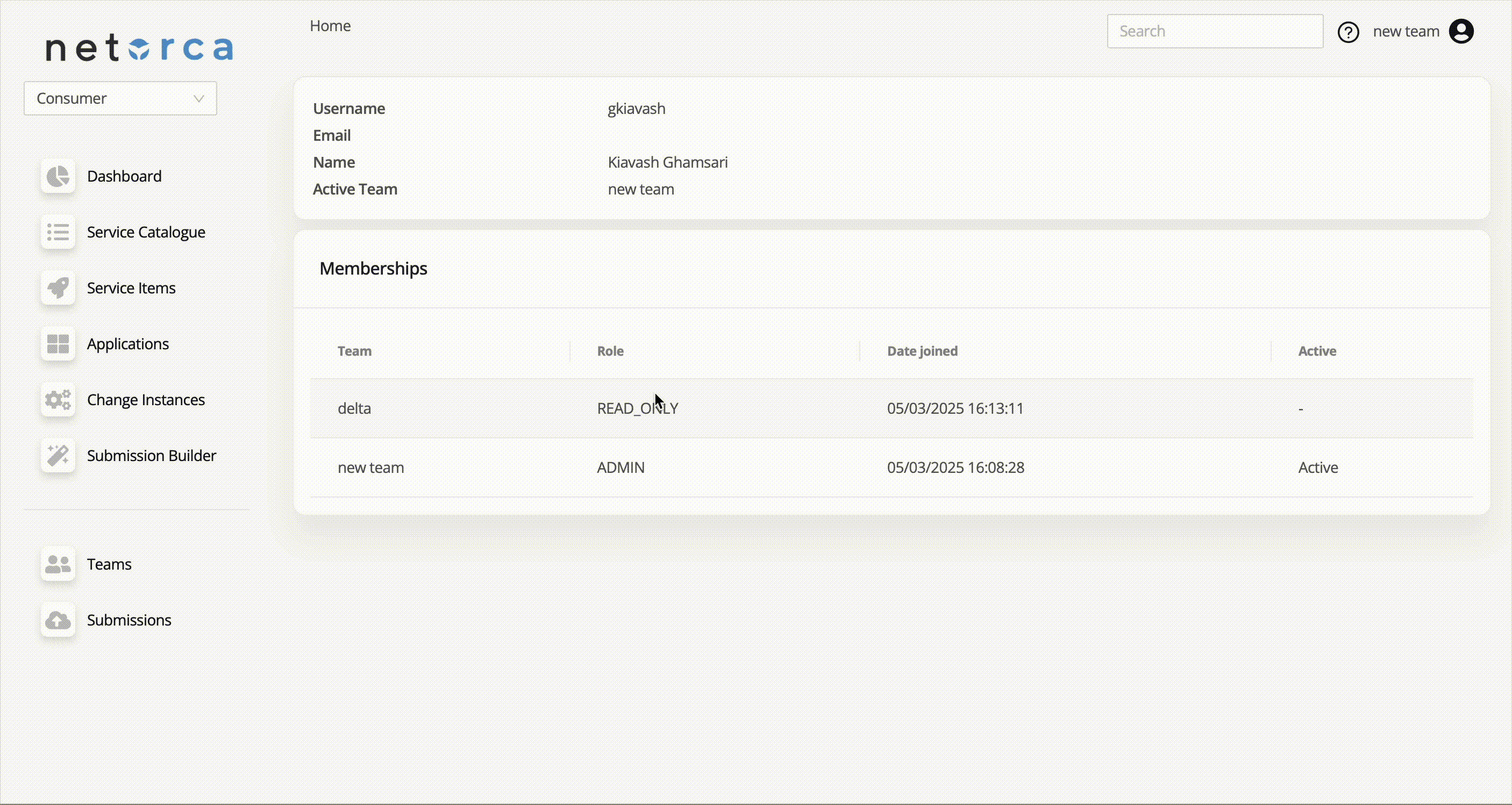
Memberships
Users can be part of one or more teams with different roles. Each team member in NetOrca is assigned a role that determines their level of access and permissions.
Roles
The available roles are:
| Role | Description |
|---|---|
ADMIN |
Has full control over the team, including adding/removing members, managing settings and API keys, processing change instances |
GENERAL |
Can view the resources and process the change instances |
READ_ONLY |
Can view the resources but cannot make any modifications |
- To access the list of membership of the active team:
- To access the list of membership of the user:
Activating a Team
Users cannot have more one membership in each Team, and there is only one active membership at a time. Therefore, when the user fetches the resources, e.g. service items, applications, the list of resources for the active team will be returned.
To activate a team which user is a member of:
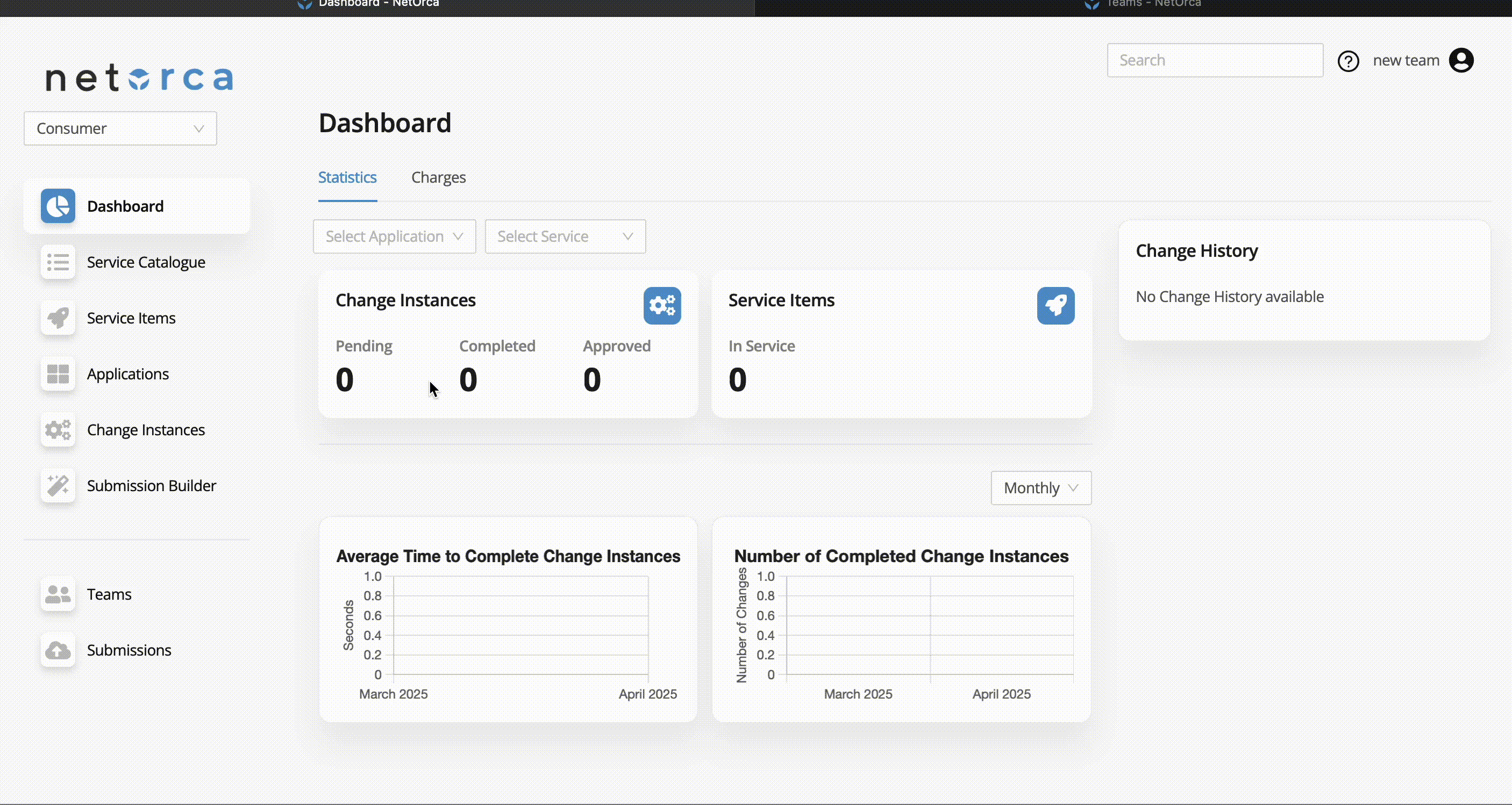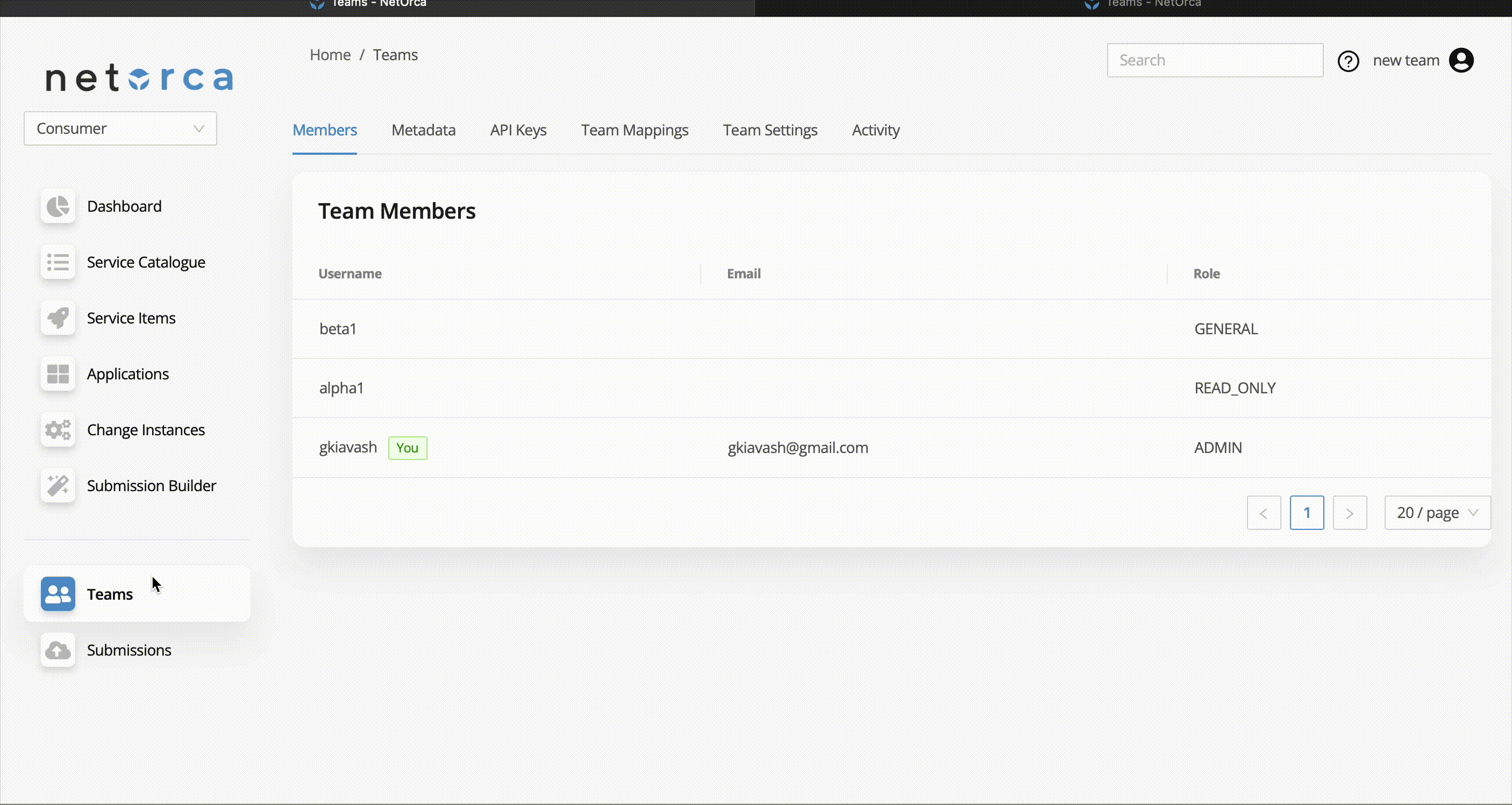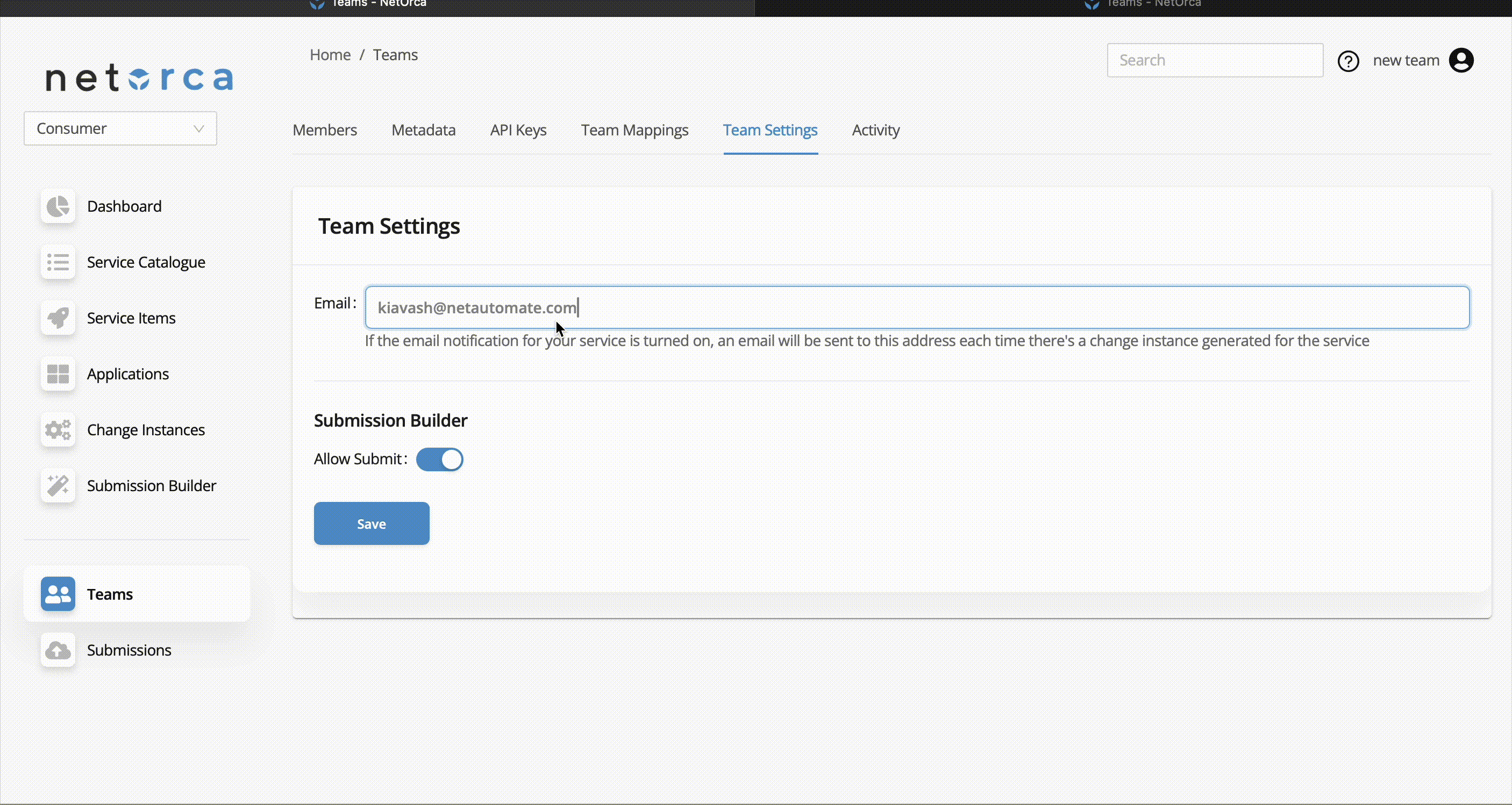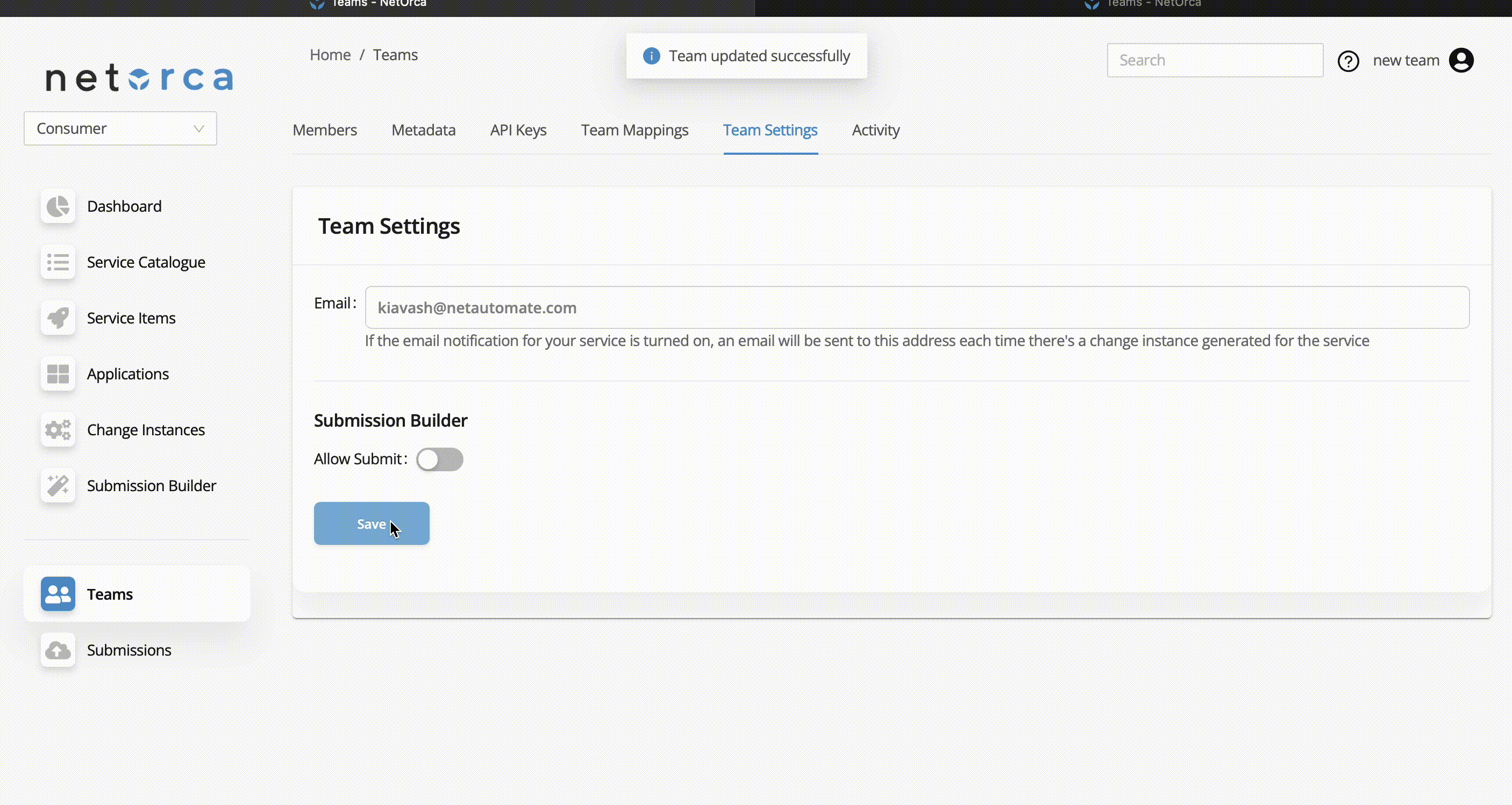
Team Settings
The Admin of the Team can configure team-wide settings to manage workflows and permissions efficiently. Available settings include:
| Role | Description |
|---|---|
email |
A designated email address to receive notifications for change instance generation, provided that the NetOrca has activated email notifications for NetOrca instances. |
allow_submit_submission_builder |
In Consumer context, enables users to submit declarations via the web interface |
allow_service_creation |
In Service Owner context, allows services to be created directly through the web interface |
To update the team settings:
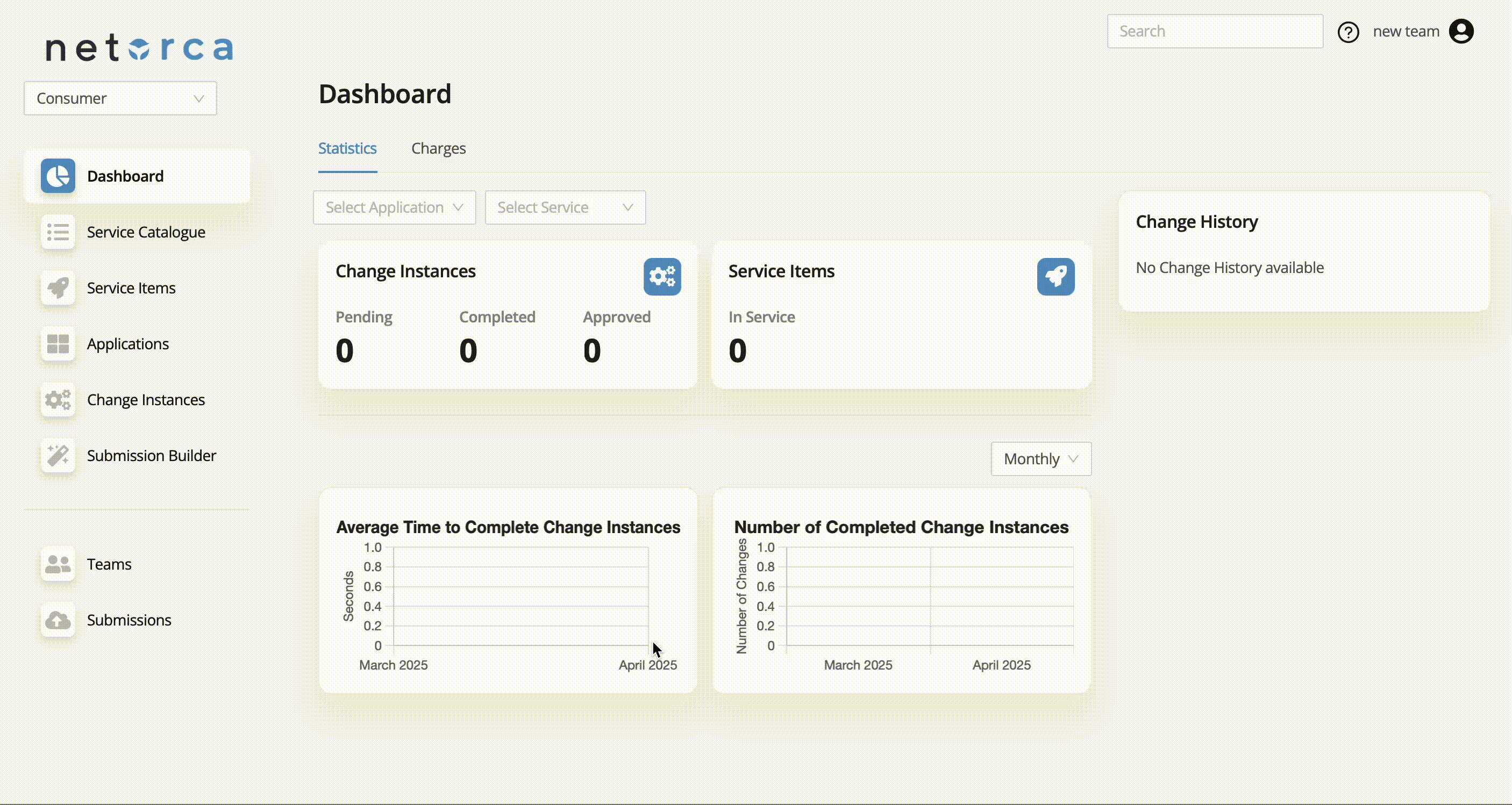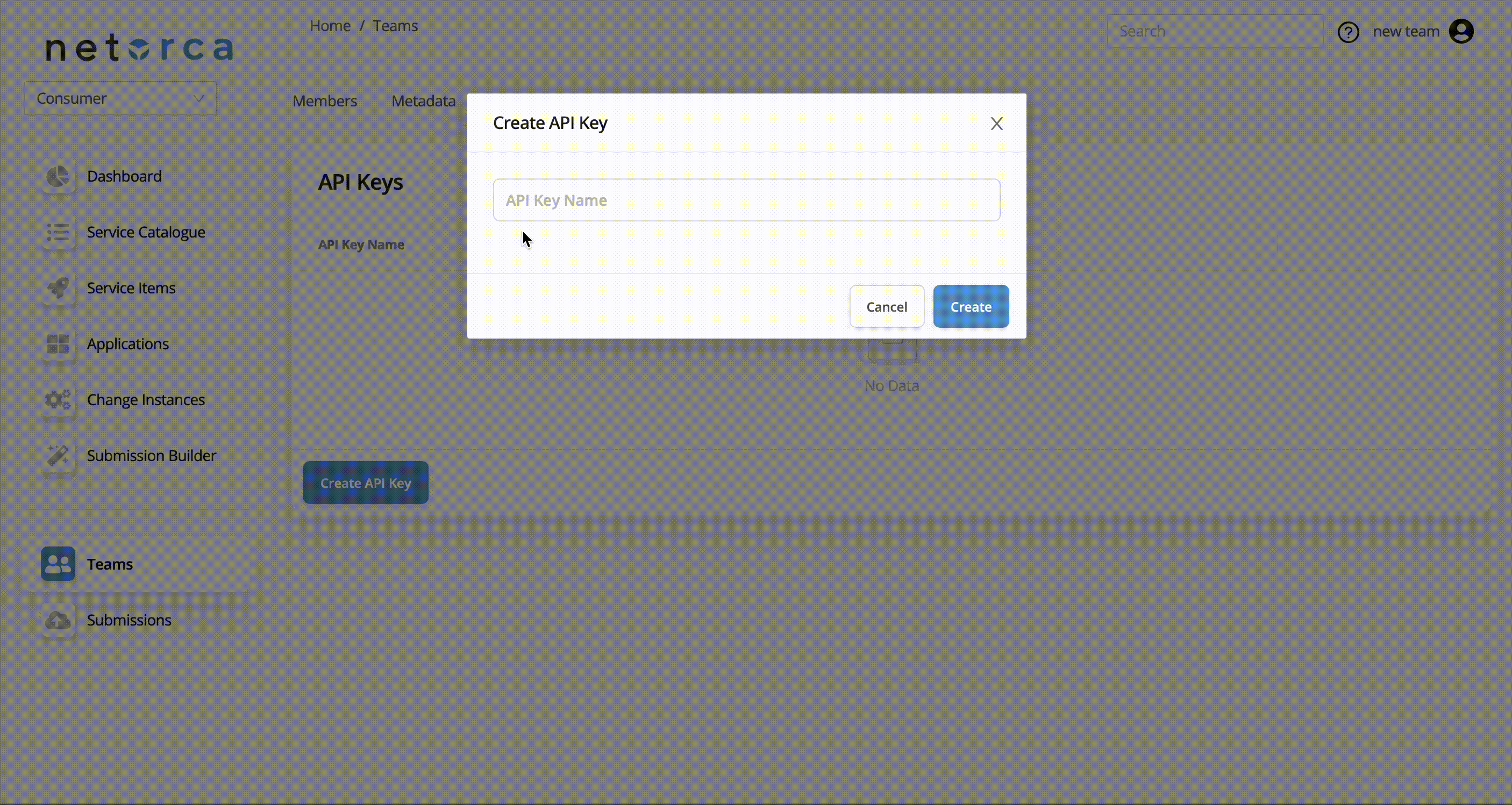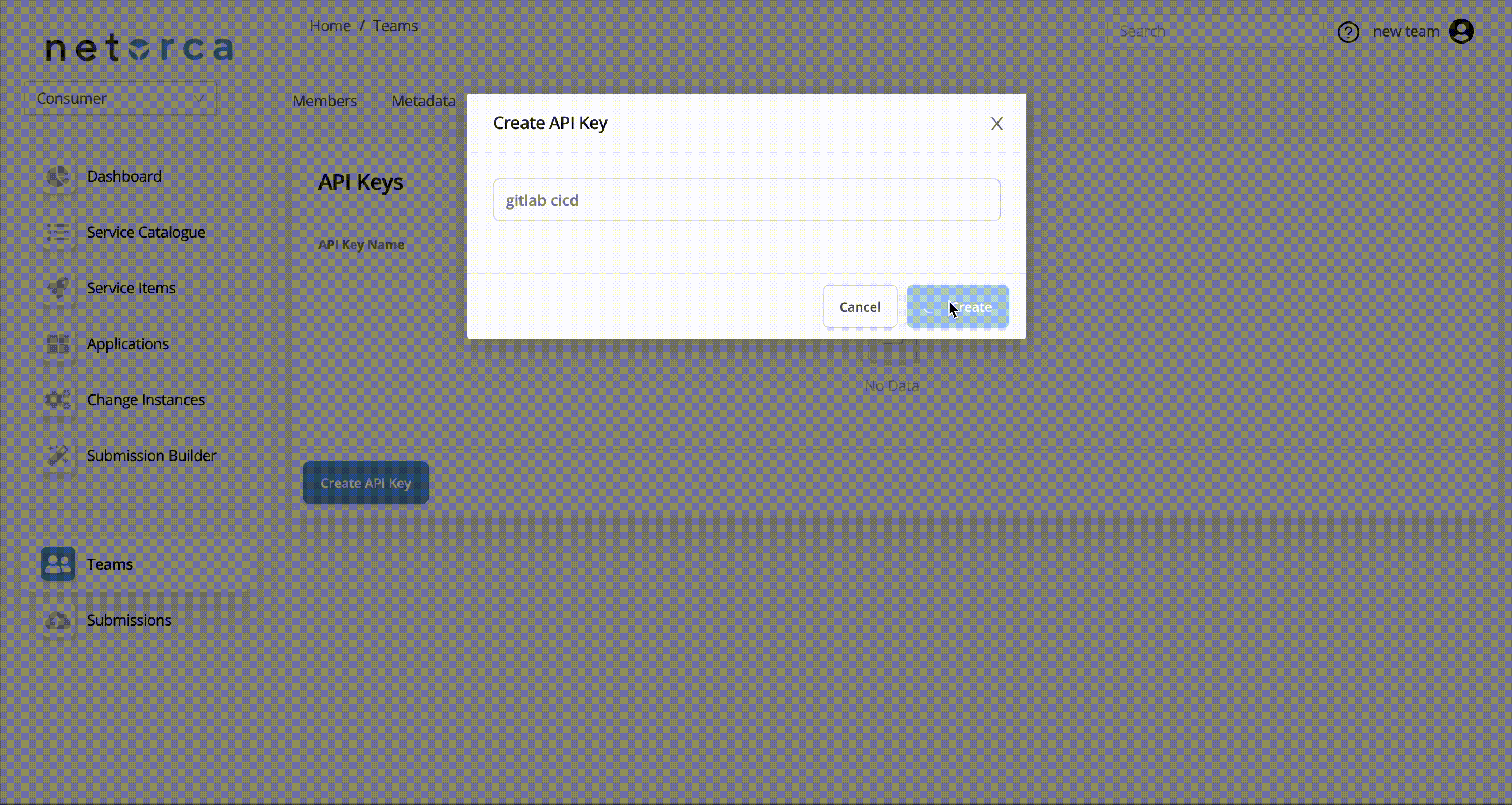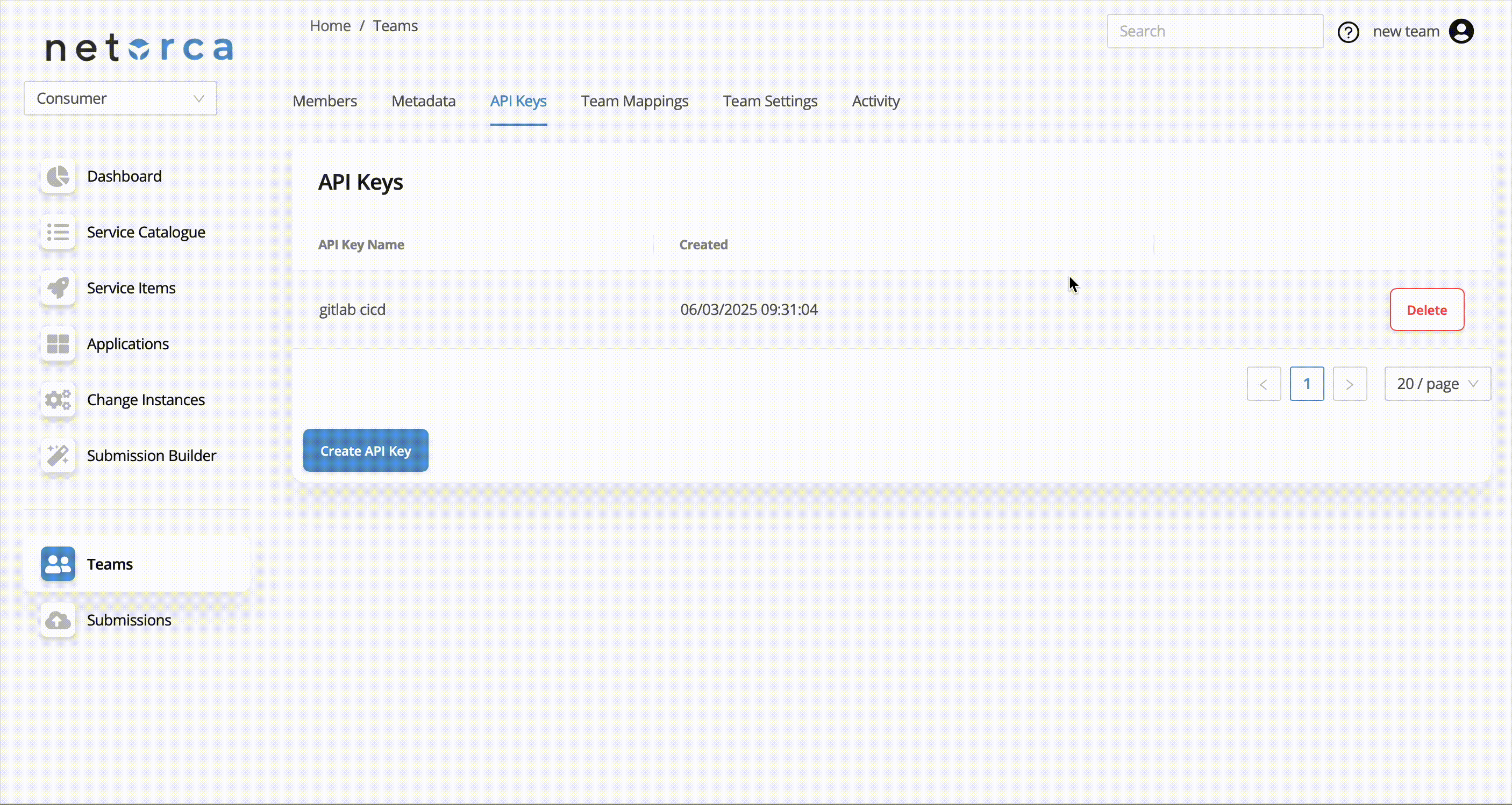
Api Key Management
Api Key is used as the authentication methodology for all communications between the CI/CD process and NetOrca.
This is more secure than using a username/password combination and allows the team to remove the api key access at any time if this is compromised.
To do this user will need to be the ADMIN the team.
To create a new Api Key:
And to delete an Api Key:
Note: The key will be displayed only in the response to the request above. Be sure to store it securely, as it cannot be retrieved later.
LDAP Integration
LDAP (Lightweight Directory Access Protocol) is a protocol used for managing and accessing directory services, such as user and group information, within an organization. It provides a structured way to authenticate users, control access, and manage permissions efficiently.
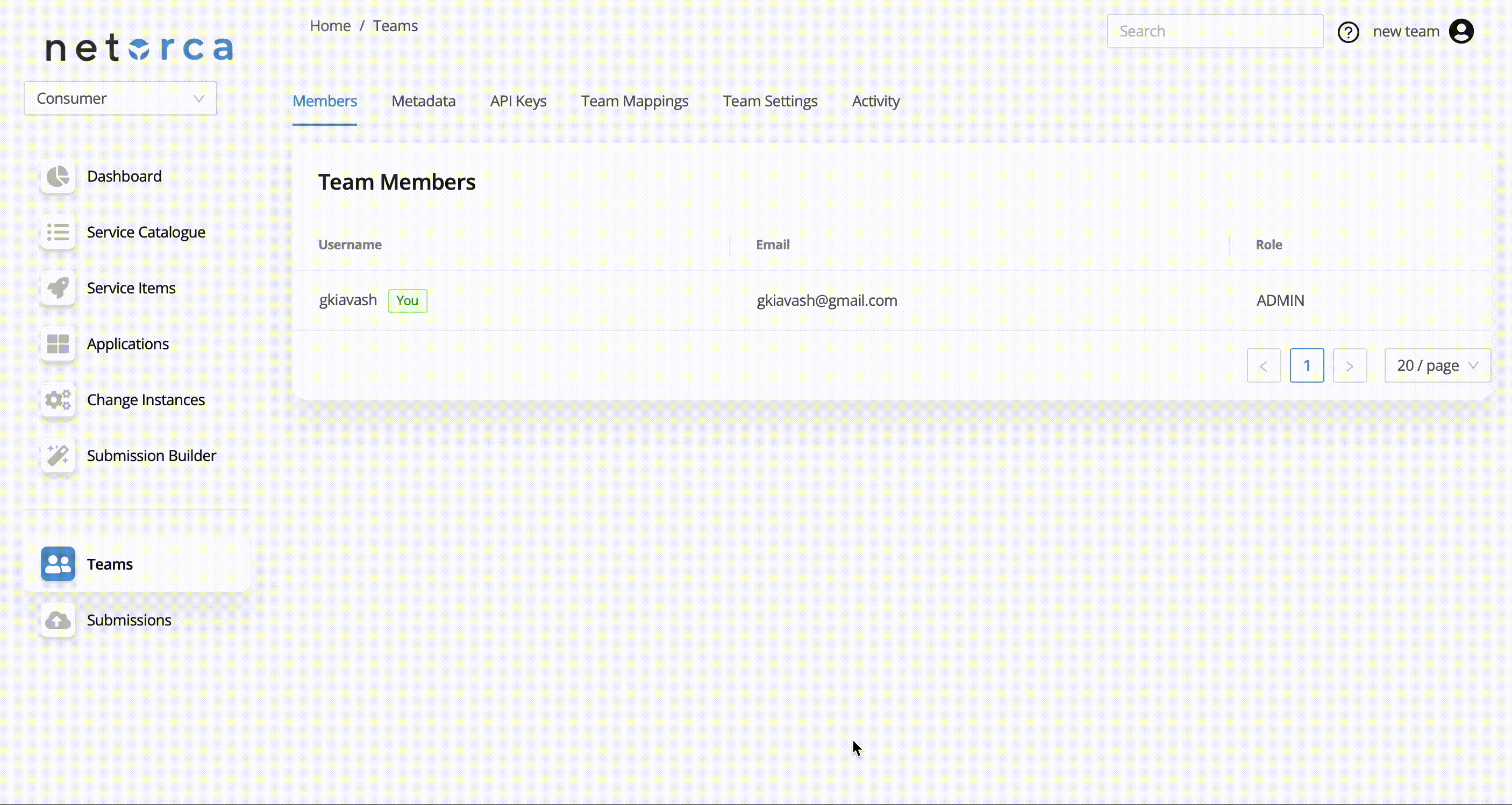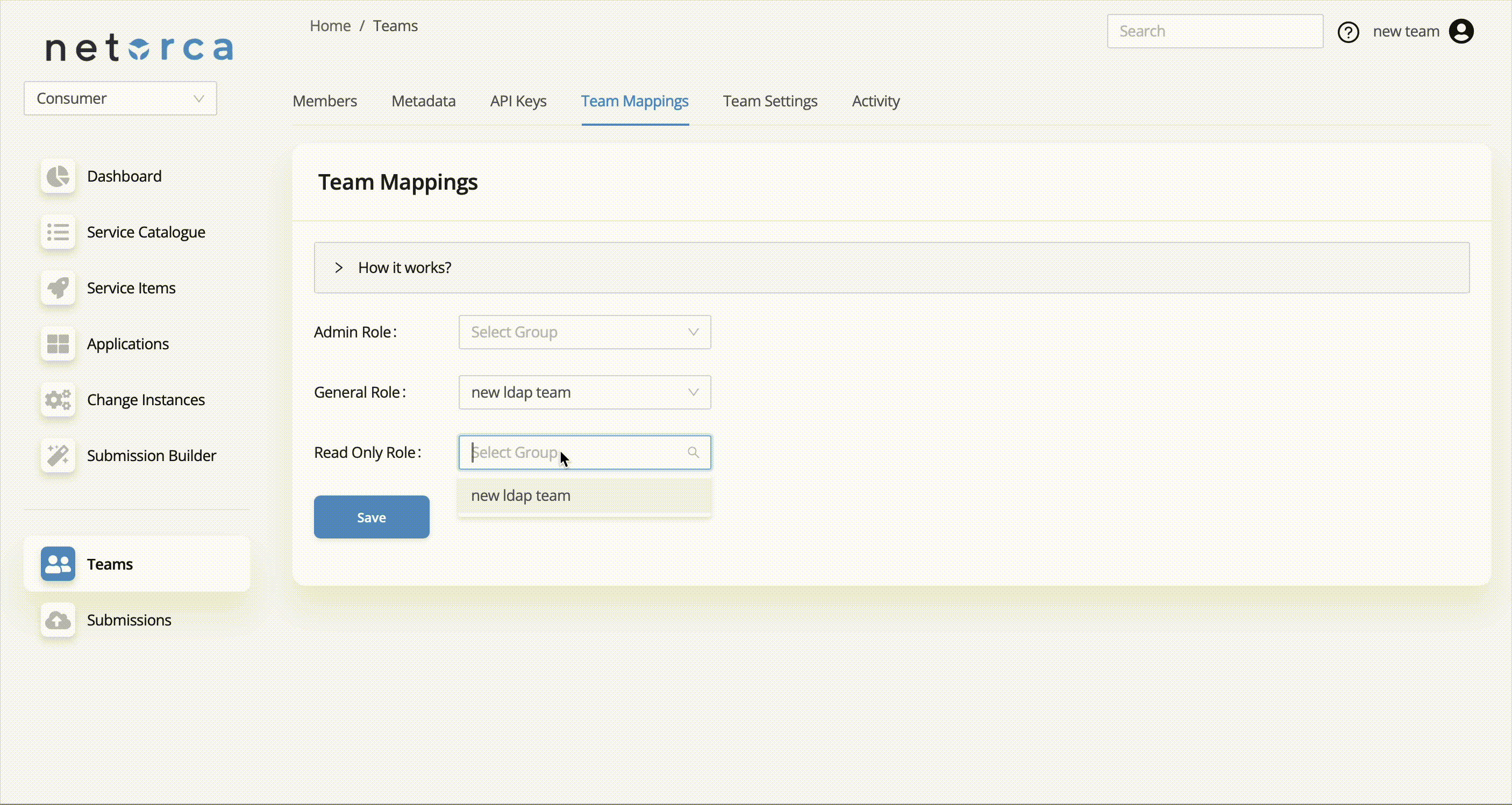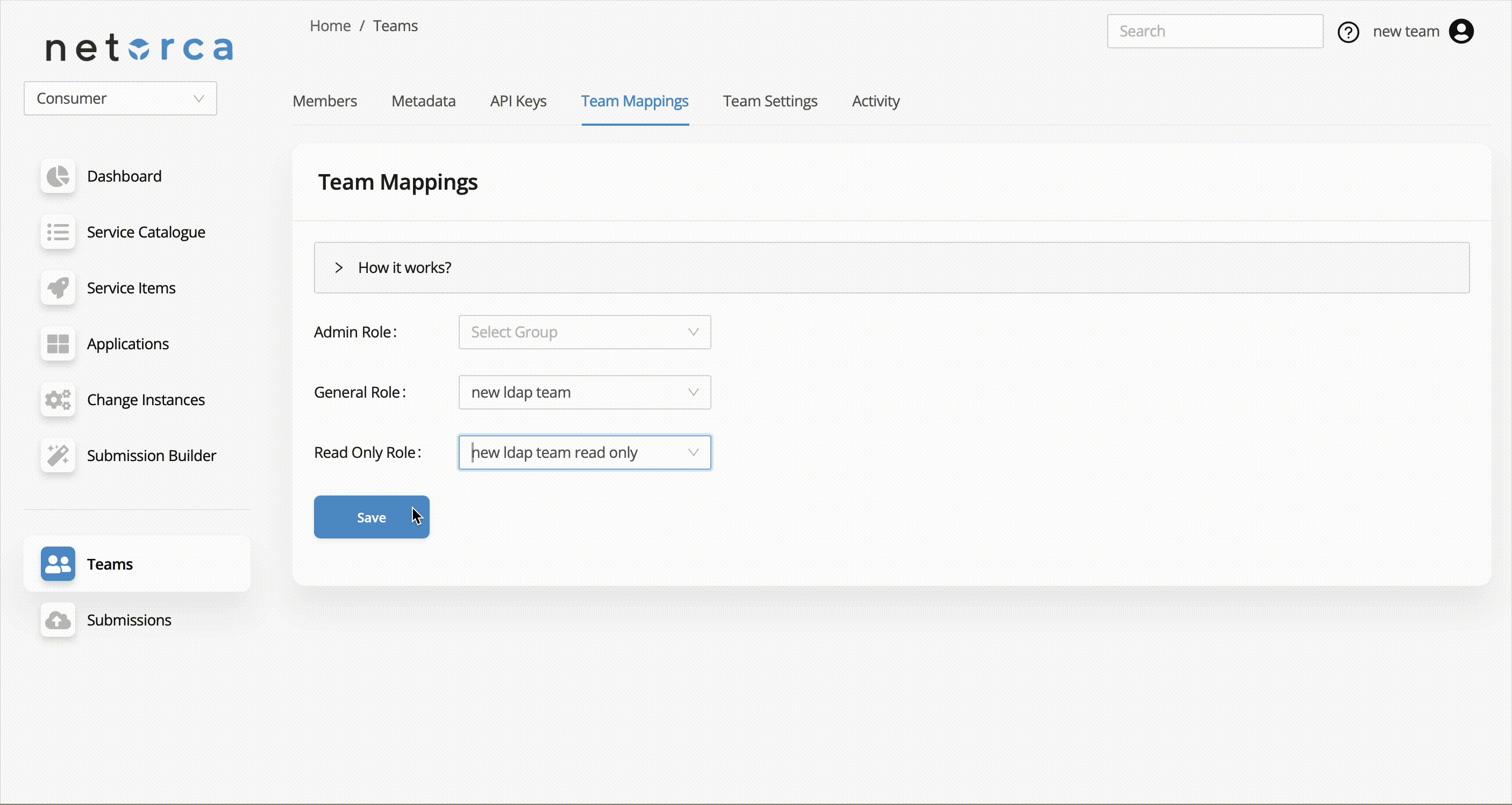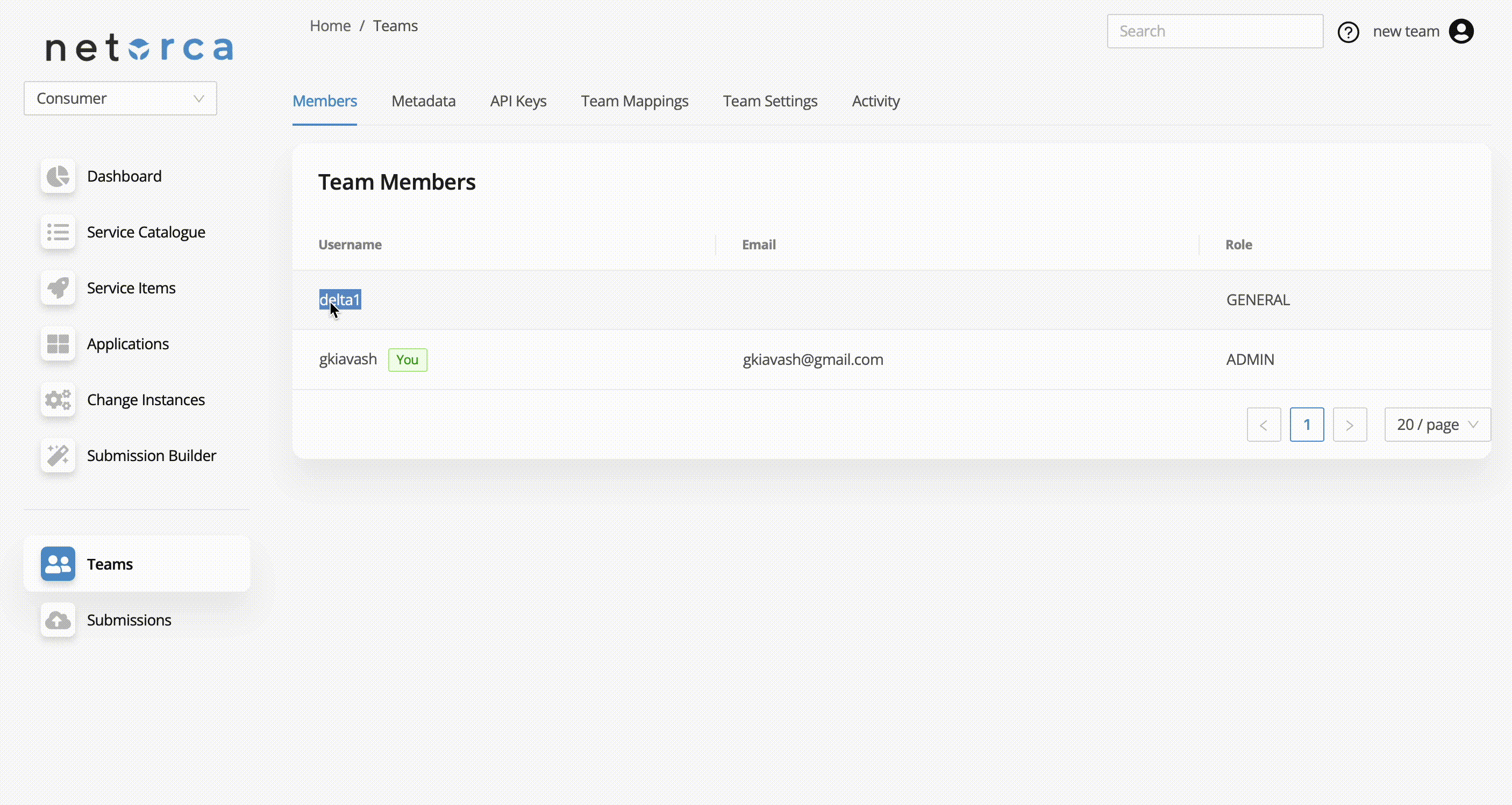
NetOrca supports LDAP integration, allowing teams to map their LDAP groups to specific roles within NetOrca teams. Each LDAP team can be assigned to a corresponding role in a NetOrca team using Team Mappings.
In NetOrca, there are three distinct roles that can be mapped to different LDAP teams: ADMIN, GENERAL, READ_ONLY
By configuring team mappings, organizations can integrate their LDAP structure with NetOrca’s role-based access control.
To do this user will need to be the ADMIN the team.
Once the team mapping is set, NetOrca will automatically adjust existing users' memberships based on their LDAP group assignments. Users who are already in NetOrca will have their roles updated according to the team mappings configuration. Also, if a user is part of an LDAP group but does not yet exist in NetOrca, NetOrca will automatically create the user and assign them the appropriate membership based on the mapped role.